The WannaCry Ransomware Attack and Tips to Stay Safe Online
On May 12th, the viral ransomware WannaCry began alerting users their data was encrypted and demanded ransom. This has been the largest ransomware attack in history. The ransomware targeted un-updated Windows operating systems at critical commercial infrastructure points in society. The attack has affected National Health Services hospitals in England, the German train system Deutsche Bahn, the Chinese Public Security Bureau, and Nissan Motor Manufacturing in the UK. The ransomware demanded $300 dollars as ransom. So far, by May 15, 2017, 227 payments totaling $59,186 has been paid to the hacker’s Bitcoin account.
Ransomware is a type of malicious software that infects a computer with an encryption virus. The virus secretly encrypts the contents of the computer and then demands payment . Ransomware is growing more popular, compared to adware and spyware, because of the potentially lucrative outcome as well as the increase of peer to peer services.
It’s currently impossible to break a ransomware encryption. The Data Rescue Center, a hard drive recovery facility in Silicon Valley, has received hard drives infected with malware. We’ve had to return the drives because there is nothing we can do. The official F.B.I. recommendation was to pay the ransom and hope that your data is restored. That’s since been updated.
The hackers designed the code to take advantage of patched security flaws. In this case, WannaCry targets a “critical” Microsoft update that was released on March 14, 2017. The patch fixed several parts of different operating systems from Windows Vista onwards.
However, many people failed to update their computer systems. Any organization running the older Windows XP is at particular risk. Microsoft hasn’t made an XP patch since 2014. However, since the WannaCry attack, they have released an unprecedented Windows XP and Windows server 2003 patch attempting to fix security concerns.
How WannaCry Spreads
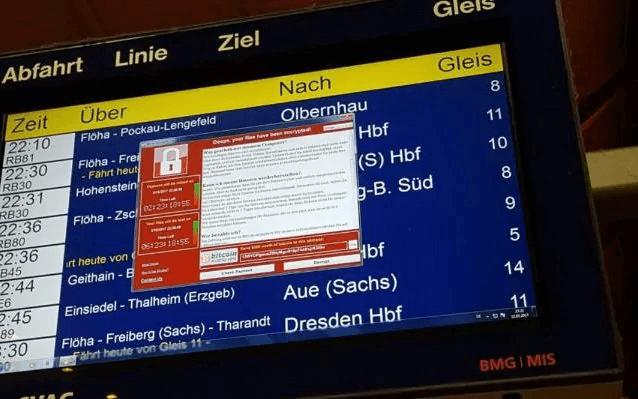
What makes WannaCry so effective is its ability to self-spread. The code infiltrates Windows computers and, once infected, WannaCry scans for other vulnerable computers on the same network. The process takes minutes for your computer to get encrypted then be held ransom. The only difference between WannaCry and other ransom softwares is the particular viral quality of the self-spreading.
Luckily, a 22-year-old British Security Researcher using the twitter handle ‘MalwareTech’ found a “kill-switch” by registering a domain name hidden in the malware. The WannaCry virus attempts to connect to the domain, and when that fails, the worm infects the system. By registering the domain name, he created a “sinkhole” by self-containing the infected systems. The perpetrators have since updated the WannaCry ransomware to exclude the kill-switch option.
The Prosoft Recommendation
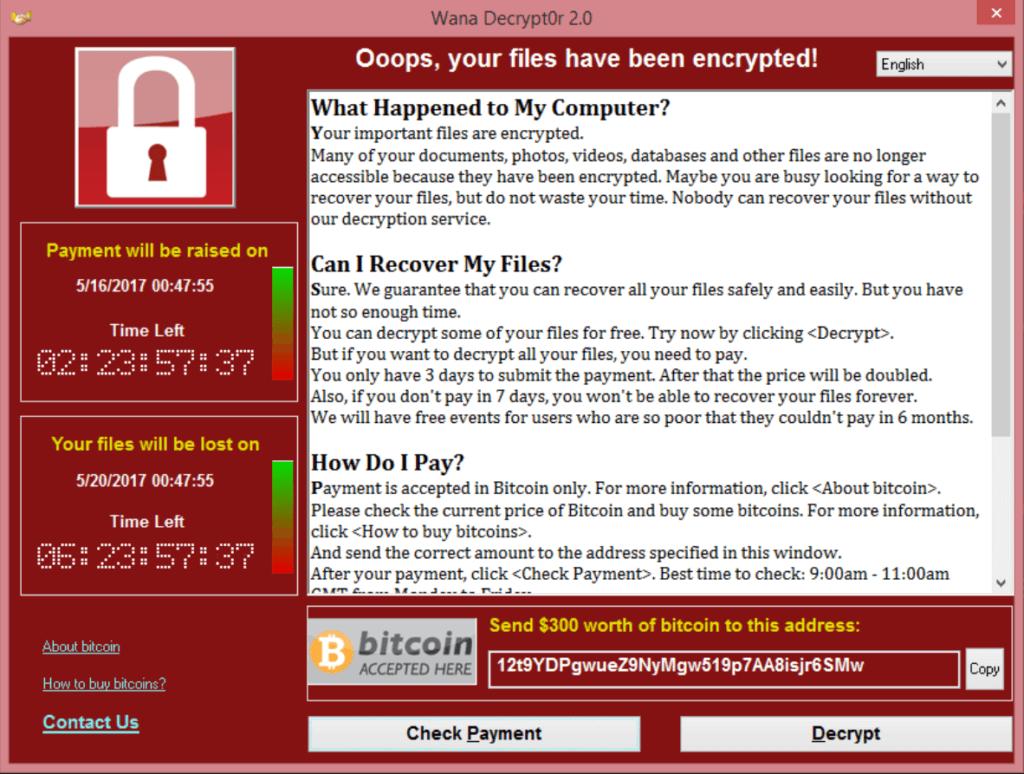
While the WannaCry malware attack affects only Windows computers, this should be a wake-up call to every Mac user. The number of ransomware and general malware code written specifically for Apple computers is growing at a rapid rate. A Prosoft Engineering colleague foreshadowed this phenomenon in his blog post, Do You Need Antivirus Protection On Your Mac? Here you can read the facts behind the modern truth: that your Mac computer needs virus protection. And even before that, we saw that Data Loss From Encryption Ransomware was on the rise.
So what can you do to prevent a ransomware attack? By going to the officially recommended No More Ransom website, you can see there is little you can do when your computer is infected. The ransomware information site states, “The general advice is not to pay the ransom. By sending your money to cybercriminals you’ll only confirm that ransomware works, and there’s no guarantee you’ll get the decryption key you need in return.” Europol, Europe’s unified police force, on twitter states, “Don’t pay the ransom.”

However, there are a few different proactive measures to preventing a ransomware infection. Nothing is a guarantee, but we recommend using all of the following steps to keep your information as safe as possible.
Have Malware Protection
The best way to prevent ransomware is to have an automated malware protection system such as the one in Drive Genius for Mac. The automatic scanning feature searches through new downloads and system files known for malware. Every file gets compared to the malware database, and the database gets updated daily. By scanning your computer for malware, you are protecting your valuable data.
Install Security Updates and Update Your Operating System
The next best thing is to update your computer’s operating system every time a patch comes around. The operating system’s creators are often the first people to notice a security flaw. If not, the malware attack is known as a “zero-day” flaw. They update the operating system to secure the patch. However, many people don’t update their system for a variety of reasons. This leaves their system vulnerable to attacks such as the WannaCry ransomware. Always update your operating system, particularly when the patch is labeled critical.
Backup your Data
Encrypted ransomware is unbreakable. As such, the only way to regain your data is to pay the ransom and hope for your data back. The other way is to have a working, valid backup of your data. If your backup has your information saved, you can re-load the operating system and other support softwares knowing your data is safe.
Note: Some variants of ransomware will encrypt all drives connected to the system. Knowing this, it is important to have valid backups that are not connected to your system.
Currently, Prosoft Engineering has Data Backup for Mac, the easy, powerful backup software. We are primed to release our first edition of Data Backup for PC in the coming months. Keep an eye out for more information on how to sign up for early access.
The Conclusion
Businesses and governments using large networks are getting the worst of it because WannaCry spreads peer to peer. Their large systems are hard to update, making them particularly vulnerable. Individual home users are more likely to install the latest security updates, and therefore be safe from this latest, greatest ransomware epidemic.
As always, Prosoft Engineering is concerned about your digital and physical security. We want to thank the many researchers working hard on uncovering the breaking news regarding the WannaCry ransomware. Remember: Backup your data, have malware protection, and install the latest updates!
About the Author
Jeremy S.
My name is Jeremy, and I write for Prosoft Engineering. I am passionate about hard drive disaster prevention and recovery. In my free time, I like to read classic literature and explore the Bay Area.